How I passed OSWE
Background
Currently, I work as a security consultant at Payatu, primarily focusing on web penetration testing and source code review. I also have around 2 years of experience in development mainly in Spring/Java. Given my background in both development and security, I thought OSWE would be a good choice.
Introduction
Advanced Web Attacks and exploitation (WEB-300) is an advanced web application security course that teaches the skills needed to conduct white box web app penetration tests.
Skills which you can gain from the course
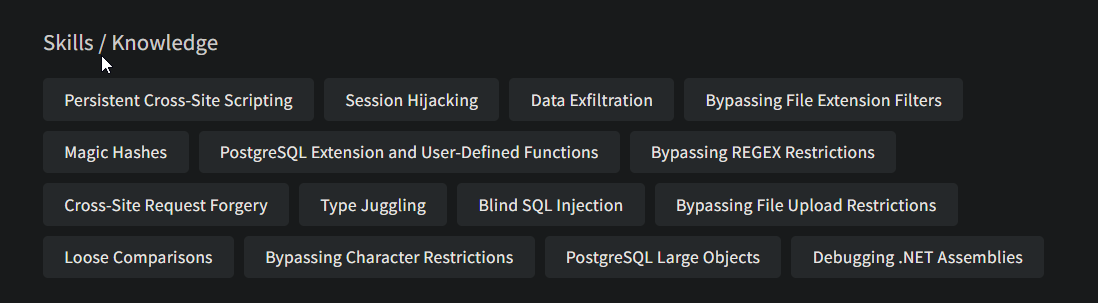
More information on the course syllabus and the other details can be found here
Is there anything I should do before purchasing the exam
Black Box
- Familiarize yourself with major web vulnerabilities like SQLi, XXE, XSS, SSTI, Deserialization, File Upload bypass , SSRF etc.
- Practice these vulnerabilities on various websites such as PortSwigger Academy and Pentester Lab. Additionally, there are intentionally vulnerable machines available on GitHub, such as “Audi1 Sqli Labs” for Sqli, “gosecure labs” for XXE, etc.
This will prepare you for the exam and at the same time make you feel comfortable with the vulnerabilities from a black box perspective.
White box
- Familiarize yourself with at least one language that supports Object-Oriented Programming concepts (OOPs) and try developing a basic CRUD application in that language. For instance, if you are comfortable with Python, learn the basics of a framework such as Django or Flask and proceed with developing the application.
- • This will help you gain a basic understanding of how the application works, OOPs concepts, databases, and more.
- Once you are comfortable in any of the languages, it will be much easier for you to read and understand the other languages as most of the OOPs concepts will be applicable and the difference will be just the syntax part in terms of code.
What I should do after buying the labs
- Go through the lab materials thoroughly as I feel material is more than enough to prepare for the exam.
- Solve the extra miles as well if you have time(I dint get time to look into it cause of other work).
- Make sure to take proper notes for each chapter you go through. For example, you can create a structure such as “Auth Bypass: How it happened,” “Privilege Escalation: How it happened,” “Obtaining RCE: How did you achieve it,” “Used Payloads”, “Python Snippets Used for scripting”, etc.
What to do after completing the lab
- If you have completed the labs, you should now have a clear understanding of understanding of the vulnerabilities that were discussed in various chapters.
- You should have an understanding of MVC, how routing works, what services are, how to identify unauthenticated and authenticated endpoints, the entry point of the application, etc.
- Offsec provides three additional practice labs(2 Whitebox and 1 Blackbox). You can attempt to solve the Whitebox labs within 48 hours, which is the same duration given for an exam as they offer a similar level of difficulty and codebase size.
- If you have comfortably solved the labs, you can proceed and schedule the exam or else work of the missed vulnerabilities.
- If you have some time before the exam, you can practice these vulnerable application. Author has specially designed these labs for OSWE exam.
- Prepare some generic scripts that can be used directly in the exam. Here is an example of a Python snippet I used to get started with scripting after manual exploitation.
|
|
What to do on the exam day
I scheduled the exam for 7:30 AM IST because it was the only available slot on 08-06-2023.
Offsec requires you to be present at least 15 minutes before the exam for ID verification, checking OS and browser compatibility, establishing a VPN connection, etc.
You will receive the link via email to connect with the proctor. One chat session will be initiated with the proctor. You have to turn on your camera and share all the screens you will be using during the exam. You can find more details here on sharing the multiple screens, giving camera permission, etc.
Proctors will instruct you show the room, ensuring there are no additional laptops, monitors, or mobile devices near your workstation during the exam. If everything goes smoothly, your exam VPN connection pack will be initiated, and you will receive the VPN credentials via email.
If you have any technical questions, you can ask the proctor through the chat. They will then communicate your queries to the technical team and provide you with a response.
There was some difficulty in connecting to the VPN provided, proctor asked the technical team to join and then we looked into it and was able to connect to the VPN after some time.
You will also receive one portal link(accessible via VPN) in the mail on which all the exam guidelines/details will be mentioned. Same portal will be used for reverting the assigned machines and submitting the flags.
You will be assigned two targets and you will also have access to two other debuggable machines that will be almost identical to the target machine, except for a few things like database credentials, secrets, etc. On debuggable machines, you can use SSH as well as RDP to review the code and for debugging purposes.
You may experience some lag in the RDP connection when browsing through the code.
You are required to perform an auth bypass (35 points) and achieve an RCE (15 points) on both target machines. You must score at least 85 points to pass the exam.
Target 1:
I took the RDP and started looking into the first target. I looked into database implementation first on how the SQL queries are being executed to look for SQL Injection.
Afterward, I started looking into the controllers/routes and the corresponding service files which are responsible for the functionality.
I looked into the codebase for around 2-3 hours, got the idea on what I can do to bypass the auth and achieve RCE.
It took approximately an additional hour to manually obtain RCE on the machine.
I quickly wrote a python script using the generic snippets from my notes to automate the same and took all the required screenshots for the report.
It took me approximately 4-5 hours to complete Target 1.
I took breaks at regular intervals for breakfast, lunch.
I paused the session and took a nap.
Target 2:
Once Again, followed the same methodology, started looking into the database implementation first, and then the routes.
It took some time to figure out the flow of this machine as compared to the Target1.
After looking into the code for 2-3 hours, got some idea on how can I bypass the auth.
Bypassed the auth manually and then RCE was pretty much easy on this machine that took me around 1 more hour.
While examining this target, RDP was lagging a lot despite my good internet speed which was more than 80Mbps.
I told the proctor the stop the session and went to bed.
The next day, I woke up late because I had already completed the target. I reviewed the scripts again, made some generalizations(cause I had time), and also took the required screenshots of the Target2 for the report.
I ran both scripts 5-6 times, reverting the targets each time, to ensure that everything is working properly. Every time, it was nice to observe the RCE with a single script.
I started writing the report using the Official Report format for OSWE provided by Offsec and finished the report in around 5-6 hours. I carefully reviewed the report multiple times to ensure it included all the necessary information, and then uploaded it following the instructions outlined in the “Submission Section” of the Offsec OSWE Exam Guide.
I informed the proctor to end the exam and my VPN existing connection expired. Note: If you end the exam, you VPN will expire and you won’t be able to resume the session.
Exam Review and Tips
- If you are comfortable reading the languages like Java, Python, Node JS,PHP, ASP.net and are familiar with web security concepts, it shouldn’t be too difficult.
- Don’t overthink too much. If you have comfortably solved the practice labs, go ahead and take the exam. The practice labs offer a similar level of difficulty and codebase size that you will encounter during the exam.
- Try to schedule your exam at least one month in advance, as the slots, especially the ones on weekends, are not easily available. You can reschedule your exam twice after scheduling it.
- Try to focus more the Auth bypass first, Look into the unauthenticated endpoint first as it carries a score of 35 points. RCE will be relatively easier compared to the Auth bypass.
- Read the exam objectives carefully as they contain all the necessary details.
- Take regular breaks in between and have your food properly.
Conclusion
After waiting for another 24 hours, finally the results arrived and I was awarded with the OSWE cert.

Originally Published at: https://payatu.com/blog/cracking-the-code-my-journey-to-conquering-the-oswe-exam/